McCabe Software - Proud Member of the
Microsoft Security Development Lifecycle (SDL) Pro Network
The Microsoft Security Development Lifecycle (SDL) is the industry-leading software security assurance process created by Microsoft and proven effective since 2004. The SDL Pro Network is a group of security consultants, training companies, and tool providers that specialize in application security and have substantial experience and expertise with the methodology and technologies of the SDL.
For more information, visit www.microsoft.com/sdl (or the SDL Pro Network page) www.microsoft.com/security/sdl/getstarted/pronetwork.aspx
Software Security Analysis using McCabe IQ by McCabe Software
For organizations that need to perform vulnerability analysis on complex software, McCabe IQ’s unique path oriented approach enables you to uncover and verify exploitable paths within your codebase. Unlike other software security tools, McCabe IQ provides thorough structural analysis and visualization as the foundation upon which security analysis and verification can confidently be performed.
McCabe IQ integrates information from several disciplines in order to produce its analysis. By combining Structural Analysis, Quality Analysis, and Security Analysis, McCabe IQ provides unique insight into the security vulnerabilities within your codebase.
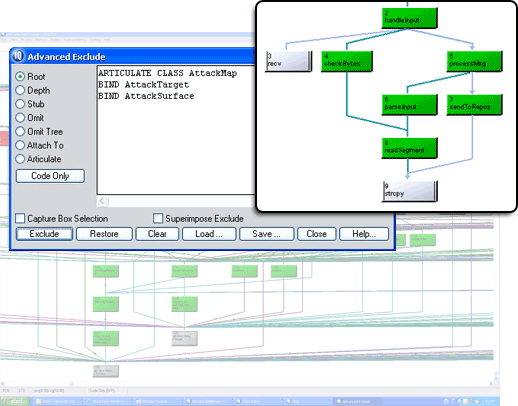 McCabe IQ takes into account the complexity and connectedness of components when analyzing vulnerability. As software becomes more complex, security flaws are more easily introduced and more difficult to eliminate, requiring considerable human effort. This is because the code reviewer may have no knowledge about the paths through the program that exploit the vulnerability. McCabe IQ takes into account the complexity and connectedness of components when analyzing vulnerability. As software becomes more complex, security flaws are more easily introduced and more difficult to eliminate, requiring considerable human effort. This is because the code reviewer may have no knowledge about the paths through the program that exploit the vulnerability.
Understanding the connectivity of paths within the source code under security review is essential to determining, quantifying, testing and measuring the scope of changes required to remediate the security flaw.
The vulnerability of software depends on the structural characteristics of the source code. The exploitability of a vulnerability is largely determined by whether or not the potential exploit is reachable from the attack surface along a path or subtree. Using the industry-proven McCabe Basis Path oriented structured testing methodology, an analyst is able to determine which potential vulnerabilities may be exploitable along code paths. This methodology can also help increase the effectiveness of your security testing by using path coverage and visualization.
No tools currently in the marketplace actually fix, edit, reengineer, identify the scope of change, test or retest the source code once a vulnerability is found. McCabe IQ’s analysis and verification capabilities for security can help fill this void.
McCabe IQ's software security analysis includes:
- Exploitable Vulnerabilities Identification
- Attack Surface Code Coverage
- Defensible Attack Space Metrics
- Source Code Pattern Recognition and Forensics
- Library Routine Usage Analysis
- Complexity Management
- Control Flow Attack Map Generation
- Attack Tree Identification and Verification
- Control Flow Integrity Measurement and Monitoring
Visit security.mccabe.com for more information or call us at 800-638-6316 to schedule a live demonstration
|